Because of my current internet provider which refuse to give me a public IP (providing me with only CGNAT), I can no longer access my stuff at home as I wish. This post describes my workaround for the problem.
External access server
Used to connect the tunnel from the inside to, and to connect to from the outside. I use a Oracle Free tier WM for this.
On the access server, I have set up a (normal) user account for the tunnel, then created a private key using Puttygen and added the public key to the .ssh/authorized_keys file for the user.
/etc/ssh/sshd_config needs to be modified by adding the line
GatewayPorts clientspecified
Do not forget to check that you are able to login to the server using the user set up for this purpose (set private key login in Putty, or use ssh -i with that key)
Firewall on the access server
If the access server is behind other firewalls, you need to open the port(s) you want to connect to.
For the Oracle VMs, this is done via the web UI:
Virtual Cloud Networks, click the VCN name, click the subnet name, click the security list (“Default security list” unless you have done it the recommended way to create separate security lists). Then (at last), “Add Ingress Rules”:
Source CIDR: 0.0.0.0/0 (unless you want to limit, but just for testing this will allow everyone to connect)
Source port: blank
Destination port: the port you want to connect to. An unprivileged user (the SSH user account) can only use ports 1025 and up.
The same port(s) also need to be opened on the access server itself.
I prefer using firewalld for this:
# firewall-cmd –zone=public –permanent –add-port={your-port-number-here}/tcp
# firewall-cmd –reload
GUI for plink (from Putty) to keep a reverse SSH tunnel open
https://myentunnel.informer.com/download/
Download the file (myentunnel_setup-3.6.1.exe), install it and then replace the included plink.exe with the current version included by the Putty installation.
Putty location: C:\Program Files\PuTTY
myEntunnel location: C:\Program Files\MyEnTunnel
Files used for the default profile: localports.txt (blank), remoteports.txt, keyfile.ppk (used for connecting to the server)
Ref: https://superuser.com/questions/235395/automatic-ssh-tunneling-from-windows
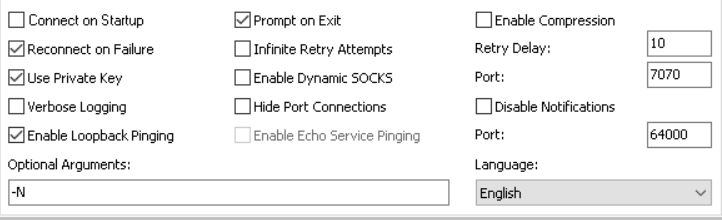
MyEntunnel configuration
Settings tab:
The obvious section, server (name or IP) and username, I suppose you know what to fill in there 🙂
No passphrase is needed, since we’re connecting with a private key only (this is also required by Oracle VMs)
As I forgot to note down the default settings, I just provide a snapshot of the settings I have in use (most are default values):
Tunnels tab:
Only the remote side needs to be filled in, syntax as the description below the input fields (per tunnel to create):
[listen-IP:]listen-port:host:port
Where listen-IP is the LOCAL ip of the access server (a private IP address if behind NAT as with the Oracle WMs, which are usually by default on the 10.x.x.x network)
listen-port is the port opened in the inside and outside firewalls (the port on which you will access the inside stuff on)
host is the inside host, can be localhost for the computer running MyEntunnel, or any other host reachable from that computer.
port is the port on the inside host
A complete line could look like this:
10.0.0.3:18180:192.168.101.180:80
(will access port 80 on the inside host IP 192.168.101.180, when going through the access server at port 18180)